Both, Vorta and Borgmatic are backup clients and rely on Borgbackup. The setup is split into the three parts "Borg backup server", "Vorta client" and "Borgmatic client".
- Borg backup server runs as a service on a NAS or another PC, connection is established only via SSH.
- Vorta is a GUI for managing Borg backups like mounting archives and scheduling backup runs. It's a convenient way to backup user directories by the desktop user.
- Borgmatic is a systemd way to backup root and system directories.
Backup server
First install borg backup:
root@NAS:~# apt-get install borgbackupNow add a user with a home directory which contains the backup repositories. Furthermore a .ssl directory containing the keys for ssh login are required.
root@NAS:~# adduser -d /home/borg borg
root@NAS:~# passwd borg
*****Create a directory for the repositories and init the repository storage for borg usage:
root@NAS:~# su borg
borg@NAS:~$ mkdir ~/repos
borg@NAS:~$ borg init -e repokey ~/reposThe init with the repokey creates an encrypted repo where the key is passphrase protected. The keys for each repo reside in the home directory of the borg user .config/borg/security. They should be saved in case of a data loss.
Now it's necessary that remote machines having the source folders to be backuped must copy the public ssh key to the user borg on the backup server for establishing borg communication via SSH without requesting a password.
debian@pc:/~$ ssh-copy-id -i ~/.ssh/id_rsa.pub borg@NASThe issue with such an unrestricted ssh access is, that the backup user is able to execute any command on the NAS via SSH, even when not desired. To solve this, the ssh-connection can be restricted to only execute borge serve on a restricted path. The user then is only be able to append backups through the ssh connection. After the public keys are copied to the .ssh/authorized_keys file on the backup server, the restricted command must be added to the keys.
command="cd /home/borg/repos;# change to borg repositoryborg serve --restrict-to-path /home/borg/repos",# start borg as restricted service to the repo directoryrestrict ssh-rsa#public key (restrict needed?)
The command line in .ssh/authorized_keys then looks like this:
command="cd /home/borg/repos; borg serve --restrict-to-path /home/borg/repos",restrict ssh-rsa AAAA [ ... ]Now the borg backup server is ready for usage.
Vorta
Vorta runs with user permissions, so the user is able to backup on it's own. Installation via flatpak:
debian@pc:~/$ sudo flatpak install flathub com.borgbase.VortaStart Vorta on desktop:
Create a new profile with a name like debianhome and add the repository from the borg backup server:
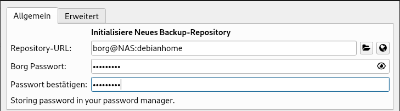
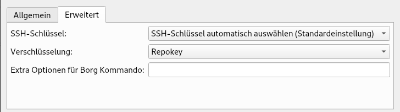
Set using of ssh key and enable encryption of backup with method Repokey:
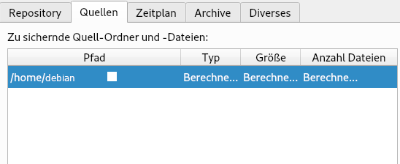
In tab "sources" there must be the backup source directory configured:
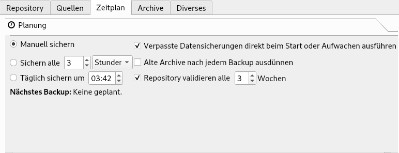
In the tab "time schedule" the time/date can be configured, when the backup is created:
When closing Vorta, it should also run in background to perform backups according the time schedule.
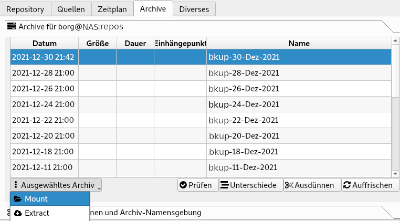
Restoring a backup is possible in tab "archive". After refreshing the archive view, a scheduled backup can be mounted to a desired directory:
Borgmatic
Borgmatic is a non-GUI systemd-service on the borg-client side to backup system directories to a borg backup server. For example the docker volumes in /var/lib/docker/volumes are the candidates for a automatic backup.
The following files are involved into configuration:
/var/lib/docker/volumes # The source directory to backup, docker volumes in this case
/etc/borgmatic/config.yaml # The borgmatic configs
/lib/systemd/system/borgmatic.timer # The timer which triggers the backup
/lib/systemd/system/borgmatic.timer.d/schedule.conf # A custom config for the timer
/root/.config/borg # The path to the borg configs and keys
/root/.ssh # The path to the borg ssh keys
/root/.cache/borg # The path to the borg cacheSee https://torsion.org/borgmatic/ for details.
SSH access
As user root copy your public key to the NAS:
ssh-copy-id -i ~/.ssh/id_rsa.pub borg@NASFurthermore on the NAS, the client's ssh access to the borg backup server must be restricted like for the Vorta client.
After the public keys are copied to the .ssh/authorized_keys file on the backup server, the restricted command must be added to the keys
command="cd /home/borg/repos;# change to borg repositoryborg serve --restrict-to-path /home/borg/repos",# start borg as restricted service to the repo directoryrestrict ssh-rsa#public key (restrict needed?)
Backup scheduling
The scheduling is controlled by a systemd-timer which triggers the borgmatic service. The default timer triggers each day at 00:00:00 and needs to be overwritten by a custom unit file snippet in systemd when changing to 21:00:00:
debian@pc:~/$ sudo mkdir /lib/systemd/system/borgmatic.timer.d
debian@pc:~/$ sudo vi /lib/systemd/system/borgmatic.timer.d/schedule.conf
[Timer]
OnCalendar=*-*-* 21:00:00For the new scheduling to take effect, systemd must be reloaded and the timer needs to be restarted:
debian@pc:~/$ sudo systemctl daemon-reload
debian@pc:~/$ sudo systemctl restart borgmatic.timerConfiguration of backup
First lets generate a sample config file /etc/borgmatic/config.yaml:
sudo borgmatic config generateThe config file sets important configuration like backup source folders, repository, archive names, checks, encryption passphrase and hooks.
location:
source_directories:
- /var/lib/docker/volumes
repositories:
- borg@NAS:Docker
one_file_system: false
storage:
encryption_passphrase: "xyzuvw"
compression: lz4
archive_name_format: 'debianpc-docker-{now}'
retention:
keep_daily: 7
prefix: 'debianpc-docker-'
consistency:
checks:
- repository
- archives
prefix: 'debianpc-docker-'
hooks:
before_backup:
- echo "Starting a backup."
before_prune:
- echo "Starting pruning."
before_check:
- echo "Starting checks."The success of the latest backup run can be checked with systemctl status borgmatic.service or by using Vorta.